By Adel Zahiry, CNM Cybersecurity & Privacy Managing Director,
Paige Kuroyama, CNM Technical Accounting Group Partner,
Jon King, CNM Cybersecurity & Privacy Director,
and Janaki Desai, CNM Cybersecurity & Privacy Manager
Executive Summary
Cybersecurity incidents continue to negatively impact the financial services industry, prompting the SEC to propose a new rule defining requirements for registered investment advisers (RIAs) and investment companies to adopt industry standard cybersecurity hygiene practices. Although the SEC acknowledges the potential costs and disproportionate impact to smaller entities, opportunities to leverage change and effective risk management are core strengths of competitive private equity firms of any size and the proposed rule protects the flexibility and agility of well-managed organizations. The improvements to the asymmetry of information about customers’ options offer further opportunity to turn mature, effective risk assessment practices into a marketable strength. Early review, planning, and adoption efforts will benefit organizations preparing for these changes.
Analysis
Introduction
New rules proposed by the Securities and Exchange Commission are intended to address cybersecurity concerns and underinvestment for investment advisers, registered investment companies, and business development companies. The proposed rules are grounded in the adviser’s fiduciary obligations to protect their client’s interests and are promulgated under the Investment Advisers and Company Acts of 1940. The 243-page memo describes the intent and structure of the proposed changes, the economic factors influencing the changes, and the expected outcomes and effects. The rule does not prescribe specific or detailed technical controls or practices; however, the proposed rules would impose the following new requirements on advisers and funds:
- Adopt and implement written policies and procedures that are reasonably designed to address cybersecurity risks
- Required reporting, on proposed Form ADV-C, of any significant cybersecurity incidents within 48 hours, to be kept confidential by the Commission
- Enhance adviser and fund disclosures related to cybersecurity risks and incidents
- Maintain for 5 years records of (1) cybersecurity policies and procedures; (2) annual reviews thereof; (3) documents related to the annual reviews; (4) regulatory filings related to cybersecurity incidents required under the proposed amendments; (5) any cybersecurity incident; and (6) cybersecurity risk assessments
The changes would apply to registered advisers subject to 17 CFR 275.206(4)-7 (“Advisers Act compliance rule”), investment companies subject to 17 CFR 270.38a-1 (“Investment Company compliance rule”), open-end funds, registered closed-end funds, business development companies, and unit investment trusts. This represents a broad and diverse array of registrants, ultimately creating the potential for some uneven impacts. The proposal acknowledged the disparity, stating that “smaller registrants—who we believe are less likely to have extensive cybersecurity measures already in place—are likely to face disproportionately higher costs resulting from the proposed rules and amendments… On the other hand, if clients and investors believe that the proposed rules and amendments effectively induce the appropriate level of cybersecurity effort among registrants, smaller registrants would likely benefit most from these improved perceptions.”
The proposal also acknowledged some overlap with 16 CFR 314 and pointed out key differences, noting that “FTC Safeguards Rule (16 CFR 314) provisions are congruent with the requirements for cybersecurity policies and procedures, annual review, and board oversight being proposed here. The FTC Safeguards Rule does not currently include [the] disclosure, regulatory reporting, or recordkeeping requirements [described in the proposed rules].”
Although broader economic considerations are discussed in the proposal, specific benefits and costs rely on a wide variety of assumptions and unknowns making them impractical to quantify. The proposal stated that “Typical estimates of cybersecurity spending in the financial industry are on the order of 0.5% of revenue; the largest compliance costs resulting from the proposed policies and procedures requirement are likely to be borne by registrants not currently following industry noted best practices.” CNM analysis of industry data and reports aligns to the SEC’s estimates, with additional insights:
- The average total cost of a data breach in the financial services sector decreased slightly from $5,850,000 in 2020 to $5,720,000 in 20211
- Data breaches that included high compliance failures cost $2,300,000 more on average than those that did not include high compliance failures1
- The estimated percent of security incidents that led to data breaches rose from an estimated 22% in 2019 and 30% in 2020 to 65% in 2021, despite a 52% decrease of attacks from 2020 to 2021 indicating that threat actors are targeting the financial services sector with increasingly effective tactics2,3,4
- 81% of breaches in the financial services sector were a result of miscellaneous errors, basic web application attacks, or social engineering2
These insights highlight the opportunities present in implementing strong, mature cybersecurity hygiene practices as a course of business. While the proposal did not describe requirements for specific practices or controls, several concepts were described that align to industry standards for cybersecurity hygiene.
Policies & Procedures
The rule changes proposed include requirements for policies and procedures to be formally reviewed and approved by the board of directors, including a majority of its independent directors. Policies would be required to address key areas of cybersecurity, including (1) risk assessment, including assessment of risks associated with certain service providers, oversight of such providers, and appropriate written contracts with such providers; (2) user security and access; (3) information protection; (4) cybersecurity threat and vulnerability management; and (5) cybersecurity incident response and recovery. An annual review and written report assessing the design and effectiveness of the cybersecurity compliance program will also be required, which must be reviewed and approved by the board of directors as well.
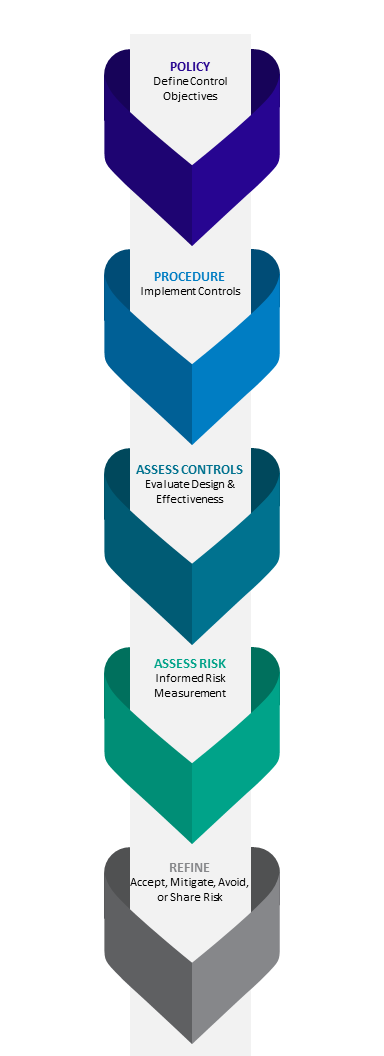
Policies can generally be viewed as “thou shalt” guidance to management in the execution of normal business operations. In the case of incident response and recovery, the policy should define the requirements for planning, preparing for, training, documenting, and reporting on the outcome and impacts of incidents. The nature of cybersecurity incidents is that they disrupt normal operations therefore laying out clear expectations and requirements for navigating the business-specific considerations during response efforts gives management the guidance required to effectively plan.
Documentation describing procedures often focuses on the general workflow or high-level processes necessary for core business operations. Critically, the proposed rule acknowledges the need for flexibility and agility and stipulates that “reasonably designed policies and procedures must empower these administrators to make decisions and escalate issues to senior officers as necessary for the administrator to carry out the role effectively”.
As a general rule, policies and procedures should strive to provide guidance for 80% of the scenarios and situations that management will face. As organizations mature, that target should increase.
Risk Assessment
Private equity faces a unique landscape in assessing risks in that the inventory of assets, systems, data, and third parties influencing risk may change frequently and have varying influences on each other. Performing risk and threat assessments – as would be required under the proposed rules – also presents unique opportunities, providing better insights into the strengths of a portfolio and how business development companies may best enhance competitive advantage and leverage complementary capabilities.
The process of performing risk assessments, separate from documenting and approving policies and procedures or assessing the design and effectiveness of controls, is a distinct cycle within the cyber risk management function. Whereas policies define the required objectives of controls and assessments of the design and effectiveness of controls aligned to policy, the risk assessment translates the results of each of those efforts. Risk assessments often generate a risk matrix or risk register in which each reasonably predictable risk is defined with an inherent risk score and a residual risk score. The inherent risk score measures the likelihood and impact of the risk without consideration of controls, while the residual risk score takes controls into consideration with added input of the controls assessment.
Risk assessments should consider the risks facing an organization through multiple lenses, including legal, regulatory, financial, strategic, and reputational. Additionally, risk assessments should be framed according to the asset or factor being assessed. For example, an organization may look at the same assets, threats, and mitigating controls and arrive at different measurements for the risk to the organization itself and the risk to the data held by the organization. For this reason, an organization may document their risk assessment in multiple formats in order to better capture competing perspectives.
In assessing the cybersecurity risks of business development companies – especially those in which portfolios are curated to position complementary capabilities in adjacent roles – additional due diligence and due care will be necessary to accurately portray the risks and threats of the total portfolio. For each entity, the risk assessment should also capture the third-party relationships and how risk is managed through the management of those relationships.
The first step for any risk assessment is defining a risk appetite and risk tolerance. The risk appetite defines the measure of risk that the organization will target while the risk tolerance defines the acceptable margin of variability. This article from COSO offers excellent introductory guidance on risk appetite.
Cybersecurity Incident Reporting
A significant challenge in tuning industry-aligned cybersecurity guidance to the reality on the ground for organizations is the limited information available about specific incidents and their impacts. Discussion in the proposed rule acknowledges this reality and the incentives many organizations face to avoid or delay reporting a significant cybersecurity incident. The SEC also acknowledged concerns about confidentiality, stating that reports of significant cybersecurity incidents under the proposed rule would remain confidential.
The proposed reporting requirements include a clear timeline for reporting. Organizations have 48 hours from the time they have a reasonable belief of a significant cybersecurity incident to submit the proposed form ADV-C outlining key details. Amendments to form ADV-C would be required within 48 hours, if new material information about a previously reported incident is discovered; information becomes materially inaccurate; and after resolving a previously reported incident or closing an internal investigation pertaining to a previously disclosed incident.
The timeline for reporting incidents emphasizes the importance of well-designed policies and procedures with consideration for training and incident response practices.
Disclosure of Cybersecurity Risks and Incidents
Consistent with cybersecurity disclosure proposals for registrants, the proposed rules would amend various disclosure forms to require advisers and funds to publicly disclose in their brochures (Form ADV Part 2A) or registration statements cybersecurity risks that could materially affect the advisory services they offer and the policies and procedures in place to identify and manage cybersecurity risks. Additionally, they would have to disclose any cybersecurity incidents that occurred over the last two fiscal years that have significantly disrupted or degraded the adviser’s ability to maintain critical operations, or that have led to unauthorized access or use of the adviser’s information, resulting in substantial harm to the adviser and its clients.
Retention Requirements
Existing best practices frameworks for cybersecurity include considerations for retention requirements specific to each organization. The new rule would establish a five-year retention requirement for documentation related to the entity’s cybersecurity risk management program, including the following:
- cybersecurity policies and procedures
- a copy of the written report documenting the annual review of its cybersecurity policies and procedures
- regulatory filings related to cybersecurity incidents required under the proposed amendments
- records documenting the occurrence of any cybersecurity incident, including any records related to any response and recovery of such incident
- cybersecurity risk assessments
Data governance and archive management has been an increasingly important field as digitization and migration to cloud environments has offered new efficiencies. Incorporating retention requirements into compliance oversight programs offers organizations an opportunity to use an existing vehicle (compliance oversight and management) to implement a valuable capability (data governance).
Conclusion
Private equity firms considering the proposed rules are best served by leaning into new requirements early due to the anticipated costs and time required to develop, approve, and implement the policies and procedures. The financial services industry continues to be a primary target for threat actors and cyber criminals, however most significant incidents may have been prevented by mature cybersecurity hygiene practices. The requirements in the proposed rule emphasize the factors that appear to have the greatest impact on improving resilience to significant cybersecurity incidents and present opportunities for private equity to enhance the competitiveness of their firms and portfolios. Although no entity can offload accountability for managing their risk effectively, advisory services are available and encouraged to progress the adoption and maturity of good risk management practices.
References
1IBM Cost of a Data Breach Report 2021 (https://www.ibm.com/security/data-breach)
2Verizon 2021 Data Breach Investigations Report (https://www.verizon.com/business/resources/reports/dbir/2021)
3Verizon 2020 Data Breach Investigations Report (https://www.verizon.com/business/resources/reports/dbir/2020)
4Verizon 2019 Data Breach Investigations Report (https://www.verizon.com/business/resources/reports/dbir/2019)
Appendix: Definitions
Definitions of specific terms used in the proposed rule:
- Cybersecurity Vulnerability: “a vulnerability in [an adviser’s or a fund’s] information systems, information system security procedures, or internal controls, including vulnerabilities in their design, maintenance, or implementation that, if exploited, could result in a cybersecurity incident.”
- Cybersecurity Threat: “any potential occurrence that may result in an unauthorized effort to adversely affect the confidentiality, integrity or availability of [an adviser’s or a fund’s] information systems or any [adviser or fund] information residing therein.”
- Cybersecurity Incident: “an unauthorized occurrence on or conducted through [an adviser’s or a fund’s] information systems that jeopardizes the confidentiality, integrity, or availability of [an adviser’s or a fund’s] information systems or any [adviser or fund] information residing therein.”
- Adviser Information: “any electronic information related to the adviser’s business, including personal information, received, maintained, created, or processed by the adviser.”
- Personal Information: “(1) any information that can be used, alone or in conjunction with any other information, to identify an individual, such as name, date of birth, place of birth, telephone number, street address, mother’s maiden name, Social Security number, driver’s license number, electronic mail address, account number, account password, biometric records or other non-public authentication information; or (2) Any other non-public information regarding a client’s account.”
- Cybersecurity Risk: “financial, operational, legal, reputational, and other adverse consequences that could stem from cybersecurity incidents, threats, and vulnerabilities.”
- Adviser Information Systems: “information resources owned or used by the adviser, including physical or virtual infrastructure controlled by such information resources, or components thereof, organized for the collection, processing, maintenance, use, sharing, dissemination, or disposition of adviser information to maintain or support the adviser’s operations.”
- Significant Advisory Cybersecurity Incident: “a cybersecurity incident, or a group of related incidents, that significantly disrupts or degrades the adviser’s ability, or the ability of a private fund client of the adviser, to maintain critical operations, or leads to the unauthorized access or use of adviser information, where the unauthorized access or use of such information results in: (1) substantial harm to the adviser, or (2) substantial harm to a client, or an investor in a private fund, whose information was accessed.”
- Significant Fund Cybersecurity Incident: “a cybersecurity incident, or a group of related incidents, that (1) significantly disrupts or degrades the fund’s ability to maintain critical operations, or (2) leads to the unauthorized access or use of fund information, which results in substantial harm to the fund, or to the investor whose information was accessed
